Get the IdP information needed for configuration at the service provider
This section covers how to obtain information for configuration on the application (service provider) side.
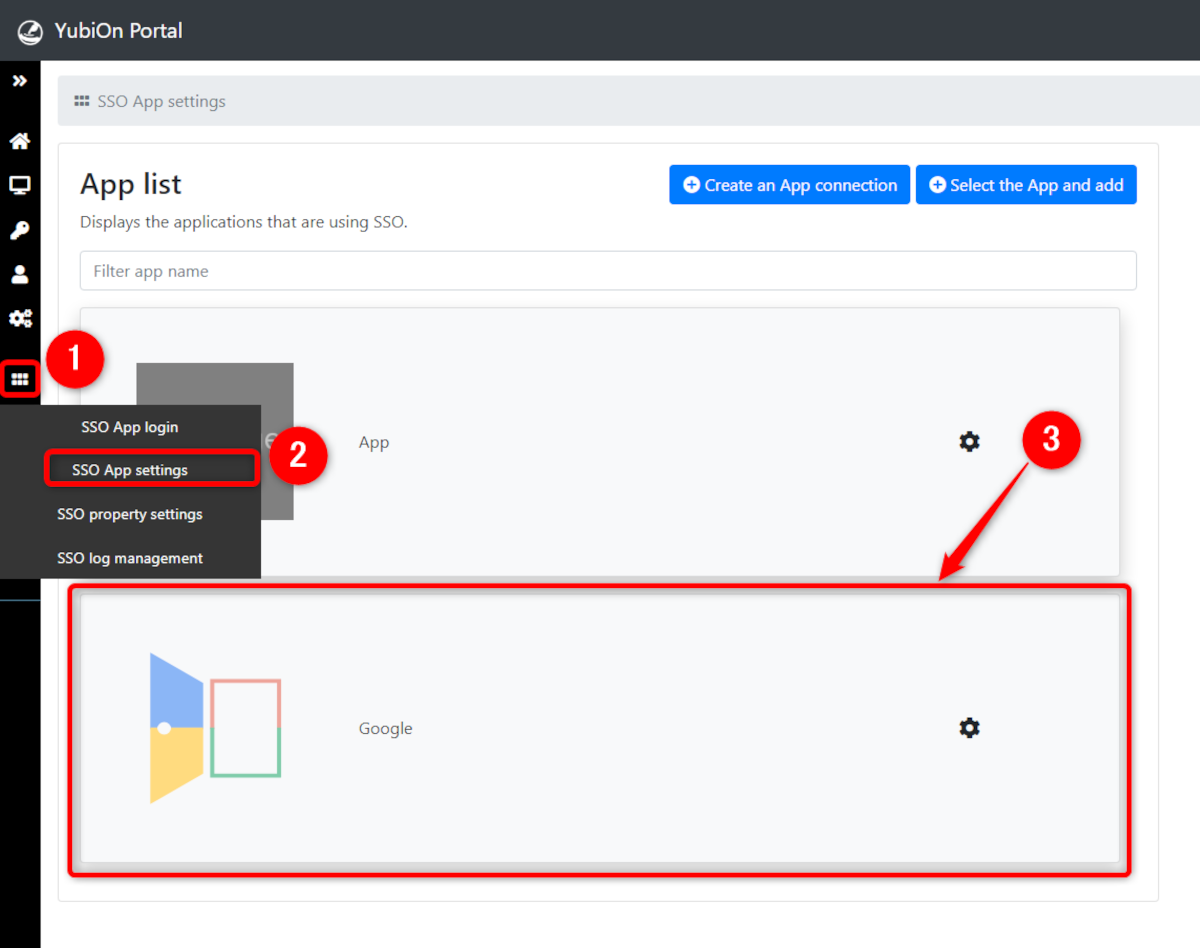
1. Access the App settings screen
Click on the “SSO App settings” from the menu on the left side of the screen, and click on the app you wish to configure from the displayed App list screen.
2. Obtaining various information
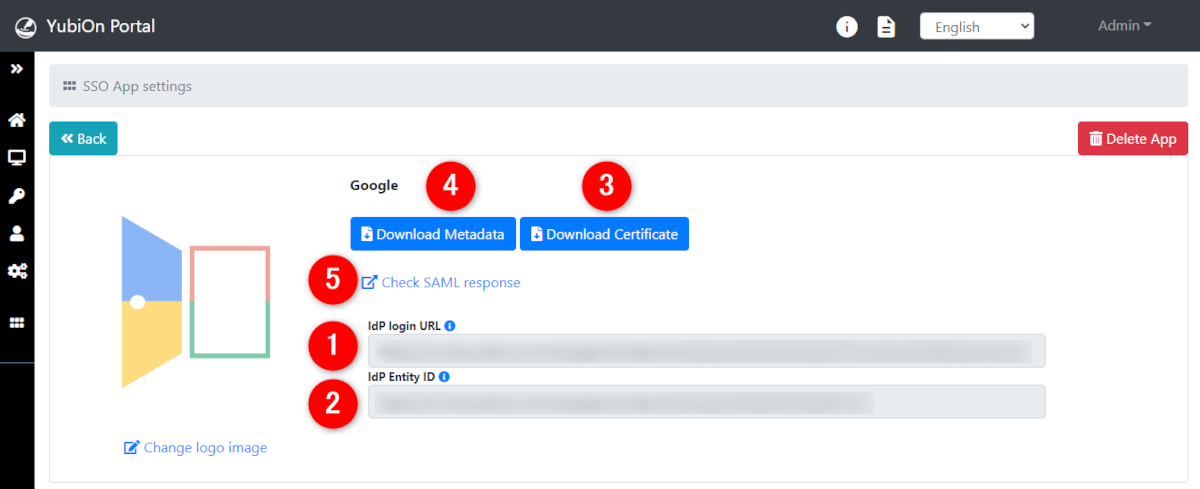
IdP login URL
This is the login URL of the Identity Provider (IdP), which is set by the service provider.
Some service providers use terms such as login URL, IdP login URL, SSO URL, or binding URL.
The setting item for the binding method (request method) may be there at the same time as well.
Please select either HTTP-POST or HTTP-Redirect bindings, which are the two binding types supported by the YubiOn Portal.IdP Entity ID
This is the entity ID of the Identity Provider (IdP), which is set by the service provider.
Some service providers may not require you to specify this.Download Certificate
This is the Identity Provider (IdP) certificate, which is set by the service provider.
On clicking the “Download” button, the certificate (in the PEM format) can be downloaded.
Upload this file if asked by the service provider for a certificate file.
If the service provider requests for this certificate to be provided as text, open the certificate file in a text editor (such as Notepad) and paste the certificates contents where required.
Although not very common, if asked for the certificate in a format other than PEM, either contact your provider or access resources regarding converting PEM to other formats.
Download Metadata
Some service providers allow uploading of identity provider metadata.
In these cases, the service provider can upload the metadata file downloaded by clicking on the button, and setting up the login URL, entity ID, and certificate in one go.Check SAML response
Click here to see the information (SAML response) that is sent to the service provider when the SSO is started.
IDs and various attributes indicating users are set based on the information of the member performing the operation.
Some service providers may implement a function to check SAML responses for errors during SAML integration.
In these cases, these contents can be used to verify problems with the configuration.
The SAML response generated here is the SAML response to the SSO request (IdP-Initiated) from YubiOn Portal.